These days,?? ??? ?? not a month goes by that we hear about a new major ransomware attack. Initially, the ransom demands were in the few hundred dollars, but those have now escalated in the millions. So how did we get to the point where our data and services could be held for ransom? And with a single attack paying out millions of dollars, should we be hopeful for this trend to ever end?
History of Ransomware
Dr. Joseph L. Popp, among his many other achievements in the field of biology, is attributed with the first use of computer software to demand a ransom. Popp dispatched 20,000 floppy disks, labelled "AIDS Information - Introductory Diskette," to hundreds of medical research institutes across 90 countries in December 1989 using the postal service. Each disk included an interactive survey that measured a person's risk of contracting AIDS based on the responses. Alongside the survey, the first ransomware - the "AIDS Trojan" encrypted files on user's computers after rebooting a set number of times.
Printers connected to the infected computers printed instructions to send a banker's draft, cashier's check, or international money order for $189 to a post office box in Panama. He planned to distribute an additional 2 million "AIDS" disks before being arrested on his way back to the US from a World Health Organization AIDS seminar. Despite the evidence against Dr. Popp, he was never convicted for the crime.
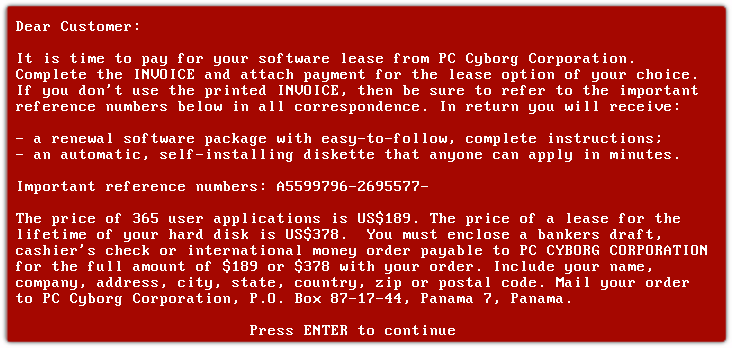
Fortunately for computer experts at the time, Dr. Popp's code used symmetric encryption and a decryption tool was created to mitigate the first-ever ransomware. With no significant ransomware attacks appearing between 1991 and 2004, could the computer world rest easy? Some would say that this was the calm before the storm.
Technological Advancements in Ransomware Evolution
By the early 2000s, cybercriminals had a ransomware blueprint and access to three essential bits of technology that Dr. Popp did not...
(1) An efficient and super fast delivery system that connects millions of computers worldwide, i.e. the world wide web. (2) Access to more robust asymmetric cryptography tools to encrypt impossible to crack files. (3) A payment platform that provides speed, anonymity, and the capability of automating decryption tasks upon payment, like Bitcoin.
Put together these elements and that's when ransomware really took off. What follows is a brief summary of a key events in ransomware's history:
- 2006- Archiveus used RSA-1024 to encrypt files, making it impossible to unlock them. Victims were forced to purchase items from an online pharmacy to receive the decryption password.
- 2008- The invention of Bitcoin, ransomware attackers could now create unique payment addresses for each victim, thus becoming the preferred payment method.
- 2011- Bitcoin matures and the number of ransomware attacks increases exponentially: 30,000 infections were reported in the first two quarters of 2011. This doubled to 60,000 by the end of the third quarter.

- 2012- Reveton takes a leaf out of the Vundo virus and uses scare tactics to force victims to pay up. After encrypting files, the Reveton worm pretended to be a law enforcement agency warning the victim they committed a crime – mostly downloading or using pirated software.
- Citadel appears on the scene. A toolkit to develop and distribute malware and manage botnets, thereby spreading ransomware even further with pay-per-install programs. Cybercriminals can pay a nominal fee to install their ransomware on already malware-infected computers.
- 2013 - 2015- A combination of RSA-2048 bit encryption, hiding both the public key and C&C servers on the Tor network and using the Gameover Zeus bot network for distribution, enabled CryptoLocker to be one of the most aggressive and fruitful ransomware
- The mobile trojan Svpeng, originally designed to steal payment card information, evolves into ransomware by 2014. Victims are locked out of their phones and accused of accessing child pornography.
- In May 2015, Ransomware-as-a-Service (RaaS) debuts, with RaaS service operators taking 20% of every Bitcoin ransom payment.
- 2016- Ransom32, fully developed in Javascript, HTML, and CSS is the first of its kind "write-once-infect-all" ransomware capable of infecting Windows, Linux, and macOS devices.
- Locky is distributed via phishing attacks using malicious Microsoft Word attachments. At its peak, it infected up to 100,000 devices per day.
- KeRanger is the first ransomware that targets Mac files and Mac's restore system, disabling the system restore feature that would allow rolling back to a previous non-encrypted state.

- 2017- WannaCry and Petya bring ransomware into the spotlight. WannaCry is a cryptoworm that semi-autonomously replicates and automatically spreads via targeted system vulnerabilities.
- WannaCry infected over 250,000 devices worldwide in early 2017 – the most significant ransomware attack in history with an estimated worldwide financial loss of $4 billion.
- NotPetya (a variant from the first 2016 Petya) is another cryptoworm that exploited the same vulnerabilities as WannaCry despite the release of security patches. Both ransomware variants highlighted the dangers of maintaining unsupported systems and the urgency of installing security patches.
- 2018- "ransomcloud" variant proves that cloud email accounts like Office 365 are also susceptible to ransomware. Fortunately, this a proof-of-concept submitted by a white hat hacker.
- Bitcoin anonymity is no longer guaranteed, and cybercriminals begin to migrate to other cryptocurrencies. New variants such as Annabelle and AVCrypt and a new version of SamSam include advanced features to avoid detection and disrupt post-attack forensics.
- 2019- Ransomware attackers begin to deploy two-stage attacks, data harvesting malware followed by ransomware. Ransomware such as MegaCortex is purpose-built to target corporate networks using domain controllers to spread.
- 2020- Security researchers report that attackers are using virtual machines to mask ransomware encryption activity on the host's files and folders, thereby avoiding detection by antivirus programs.
- 2022- Azov Ransomware presents a new shift towards destructive wipers, using polymorphic code, so as not to be potentially blocked or detected by static signatures.
Evolution of Ransomware Tactics
In addition to using advances in technology to their advantage, ransomware attackers are more aggressive and using creative methods to improve the success of ransom payouts, though thankfully that success rate is finally on the decline.
Cybercriminals have been shifting their focus to critical infrastructure and larger organizations. For example, in 2016, several hospitals were hit by ransomware, including Hollywood Presbyterian Medical Center, Ottawa Hospital, and Kentucky Methodist Hospital, to name a few. In all cases, hospital devices were locked or medical files encrypted, putting patient lives in danger.
Some hospitals were fortunate and had in place rigorous backup and recovery policies. But, unfortunately, others needed to pay the ransom to restore health services as quickly as possible.
Ransomware Evolution Timeline: 1989 - 2019
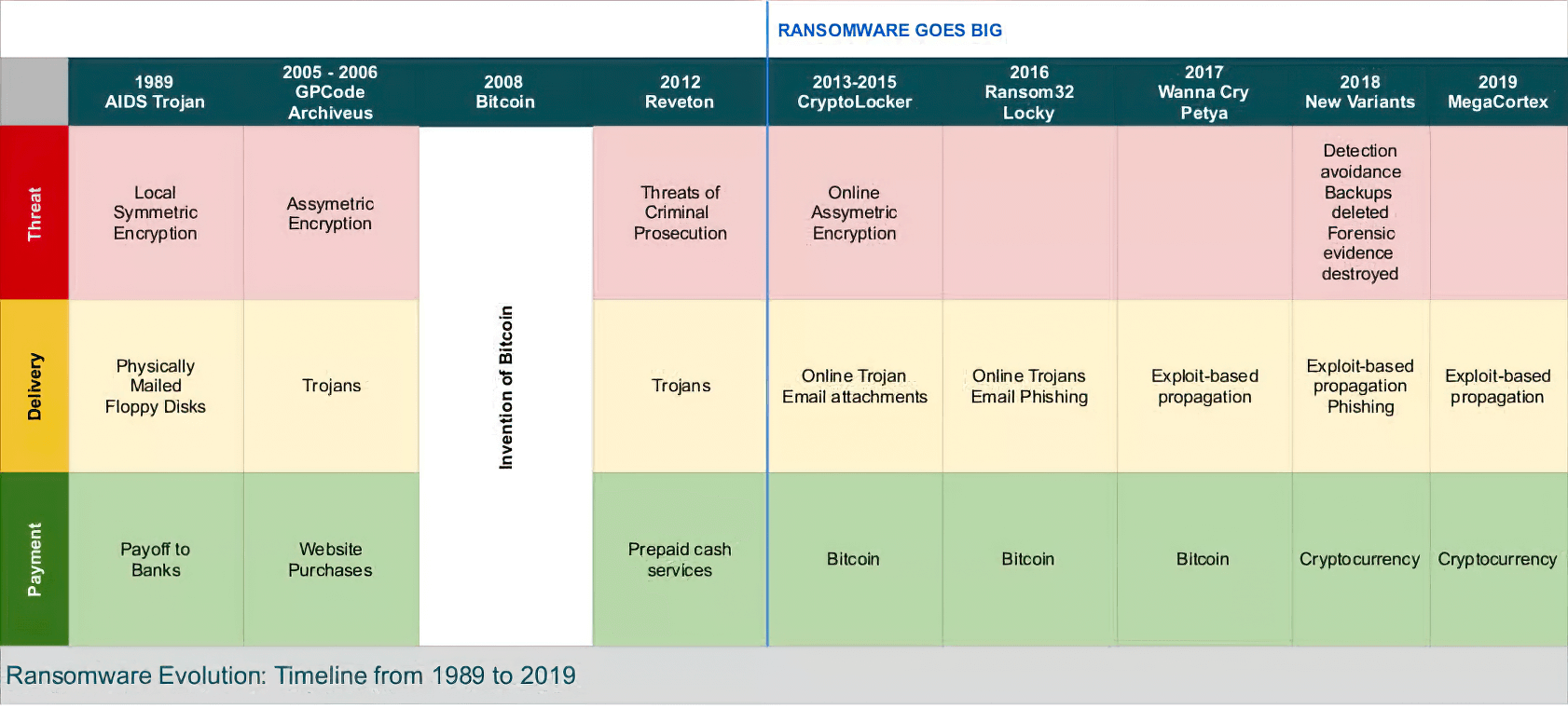
(click to enlarge)
In March 2018, many online services for the City of Atlanta were taken offline after a ransomware attack. The ransom of $55,000 in Bitcoin was not paid, but early projection put recovery costs around $2.6 million.
In May 2021, the DarkSide ransomware took down critical infrastructure responsible for delivering 45% of the gasoline consumed across 13 US states for one week. The victim of this particular attack, Colonial Pipeline, paid $4.4 million to regain their systems. Massive payouts like these only continue to drive attackers to find even more creative ways to cash out using ransomware.
Another tactic used is called 'Encrypt and Exfiltrate.' Attackers realized that the same network weaknesses that aided ransomware infection could be used to exfiltrate data. Aside from encrypting victim files, attackers steal sensitive data and threaten to publish the data if the ransom is not paid. Thus, even if an organization could recover from a ransomware attack using backups, it cannot afford a public data breach.
Vastaamo, a Finnish psychotherapy clinic with 40,000 patients, was the victim of a newer tactic called 'Triple Extortion.' As is the norm, medical files are encrypted, and a hefty ransom is demanded. However, the attackers also stole patient data. Shortly after the initial attack, patients received individual emails requesting smaller ransom amounts to avoid public disclosure of personal therapy session notes. Due to the data breach and financial damage, Vastaamo declared bankruptcy and ceased operations.
Large-capacity NAS drives from individuals has proven to be an attractive target in recent years, too, as QNAP and Asustor customers have unfortunately discovered. Deadbolt ransomware struck Asustor's internet-connected products in early 2022 and has hit QNAP's drives in multiple waves over the past couple of years.
The Future of Ransomware
Cybersecurity Ventures reported ransom attacks were up 57% since the beginning of 2021 and cost businesses an estimated $20 billion in 2020, 75% higher than 2019. Ransomware attacks are also becoming very specific with victim selection, targeting organizations within industries like healthcare, utilities, and insurance/legal that offer critical services because they are more likely to pay a sizable ransom.
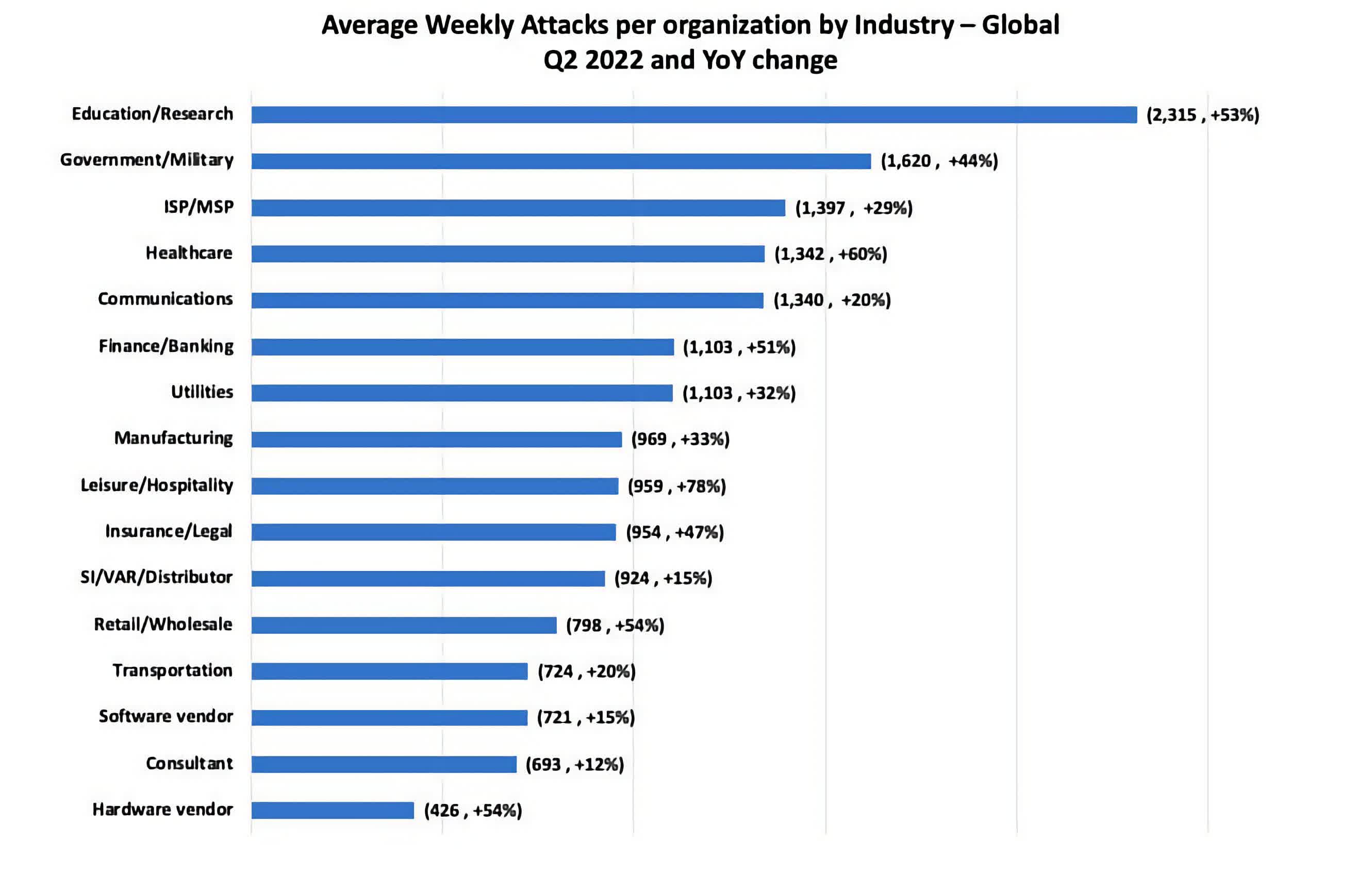
Ransomware attacks per organization per week by industry
Q2 2022 data via Check Point Research
The Education and Research sector continue to be the most heavily attacked industry, seeing a 53% increase year-over-year (2021-2022), followed by Government/Military, Internet Service Providers and Healthcare institutions.
About 40% of all new ransomware variants include data infiltration components to take advantage of double and triple-extortion techniques. In addition, REvil, a RaaS group, offers Distributed-Denial-of-Service (DDoS) attacks and voice-scrambled VoIP calls as a free service to its affiliates (the actual attackers that break into a system) to further pressure victims to pay the ransom within the designated time frame.
Why the sudden increase in ransomware attacks over the last decade? It is lucrative! Even if a small percentage of ransomware attacks succeed, they still yield a significant return on investment. Take, for example, the largest public ransom payouts to date:
- CWT Global - $ 4.5 million
- Colonial Pipeline - $ 4.4 million
- Brenntag North American Division - $4.4 million
- Travelex - $2.3 million
- The University of California at San Francisco - $ 1.1 million
Yet, these attacks only account for a tiny number of successful ransomware campaigns. Unfortunately, these same high profile payouts motivate attackers to keep looking for new ways to infect, spread and extort.
Another factor to consider: an ever-widening attack surface. In 2017, 55 traffic cameras were hit in Victoria, Australia by WannaCry due to human error. While the attack's impact was minimal, it does provide a hint of the devices that cyber criminals will target. Given the slow security update process and the increasing number of vulnerable Internet of Things (IoT) devices across the globe, this will inevitably open opportunities to ransomware operators.

Experts also fear that ransomware will start appearing in cloud services, mainly targeting Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS). Factor in new entrants, a new generation of youngsters inspired by TV shows like Mr. Robot. They have access to more resources like "Hack the Box" than any generation before them. These new entrants are eager to learn and even more eager to test out their skills.
Ransomware is at the center of a sophisticated and booming underground economy with all the markings of legitimate commerce. Imagine a community of highly skilled and collaborative malware developers, RaaS providers, ranked affiliates, IT and customer support teams, and even operators responsible for the attacker group's press releases and 'branding.'
As we give up personal data to various service providers and rely on technology for our everyday tasks and routines, we're unintentionally empowering ransomware attackers to kidnap and hold us hostage. Thus, we can only expect ransomware attacks to increase, become more aggressive and creative in ensuring ransom payments – possibly requesting the first payment to decrypt data and a second separate payment not to publish.
Unlocking Tools Become Available
In early 2023, security firm Bitdefender released a tool to help MegaCortex ransomware victims unlock their files, which is great news for those that have had files locked down for years.
The tool is also available from No More Ransom. The site plays host to unlocking tools for more than 170 pieces of ransomware and variants including well-known examples like REvil and Ragnarok.
Ransomware victims have realized that even if they pay the ransom, there's no guarantee they will get their data back or that the ransomware actor will delete the "stolen" files without selling them to third parties on the dark web. The public perception of the ransomware phenomenon has matured as well, so data leaks don't carry the same risks for brand reputation of the last few years.
The Light at the End of the Encryption Tunnel

The Colonial Pipeline hack highlighted the vulnerability of modern society. The attack led to anxiety spreading across affected cities, which led to panic buying fuel, fuel shortages, and rising fuel prices.
Ransomware costs are not limited to ransom payouts. Damage and destruction of data, downtime, reduced productivity post-attack, expenses related to forensic investigation, system restoration, improving system security, and employee training are hidden and unplanned costs that follow an attack.
Law enforcement agencies are also concerned about the possibility that a cyberattack on hospitals will cause deaths. The negative impact on human lives and society by ransomware cannot be denied and no longer ignored.
Towards the end of 2020, the Ransomware Task Force (RTF) was launched. A coalition of over 60 members from various sectors – industry, government, law enforcement and countries – is dedicated to finding solutions to stop ransomware attacks. In April 2021, the RTF released the "Combating Ransomware: A Comprehensive Framework for Action" report detailing 48 priority recommendations to address ransomware.
The concerted effort is paying off.
While no arrests have been made, the FBI managed to recover 63.7 Bitcoin (~$2.3 million) of the ransom paid out in the Colonial Pipeline attack. The FBI and other law enforcement agencies worldwide were able to disrupt the NetWalker ransomware-as-a-service element used to communicate with victims. In 2021, the Emotet botnet was also taken down, an essential tool for delivering ransomware to victims via phishing.
In October 2021 authorities arrested a dozen individuals linked to more than 1,800 ransomware attacks across 71 countries. Police spent months combing through data collected during the arrests and the keys discovered by law enforcement led to the development of new unlocking tools for the MegaCortex ransomware as mentioned before.
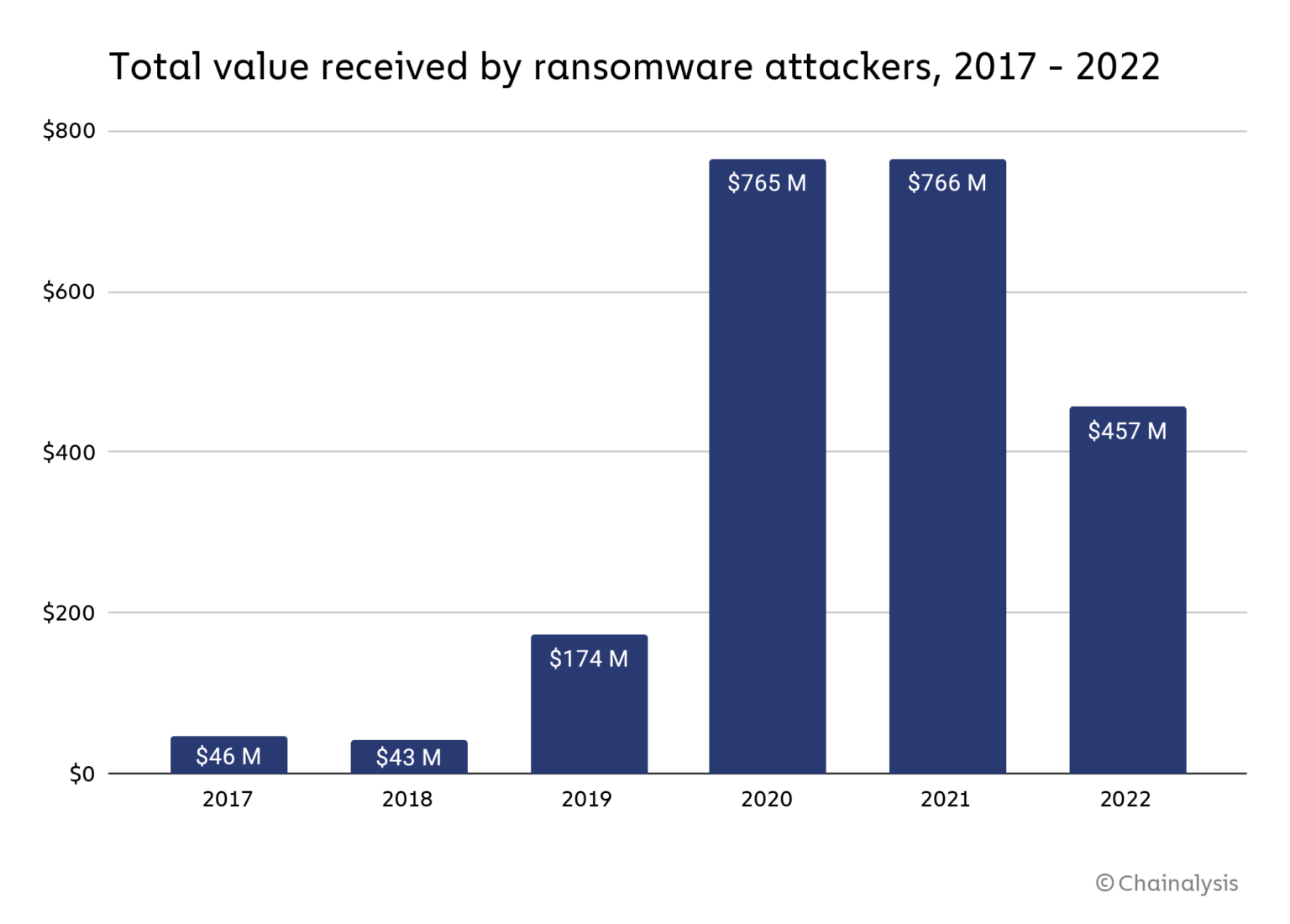
According to data provided by firm Chainalysis, ransomware revenues for 2022 have shrunk from $765.6 million to at least $456.8 million, or a -40.3% drop year-over-year. The volume of attacks is as impressive as ever, but the number of victims that refuse to pay the ransom has grown as well. Chainalysis has seen a sharp reduction in the number of ransomware victims willing to pay: they were 76% in 2019 but just 41% in 2022.
These may seem like a drop in the ocean compared to the number of ransomware attacks in the recent past, however public awareness and global organizations, government and private, are acknowledging and actively working to neutralize the ransomware threat, which are much necessary steps in the right direction.